cybergrad
custom built learning management system for cybersecurity training // 2024
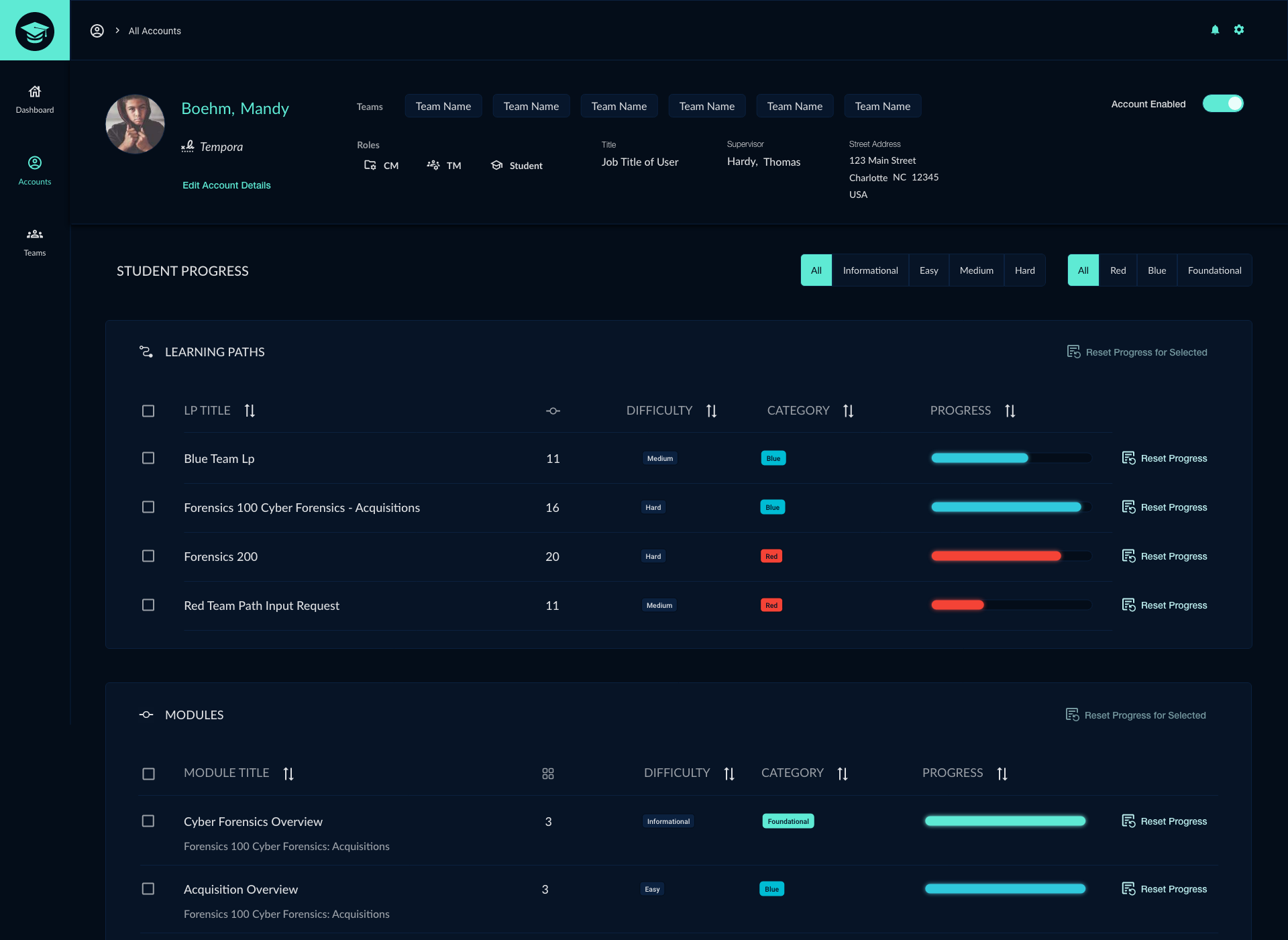
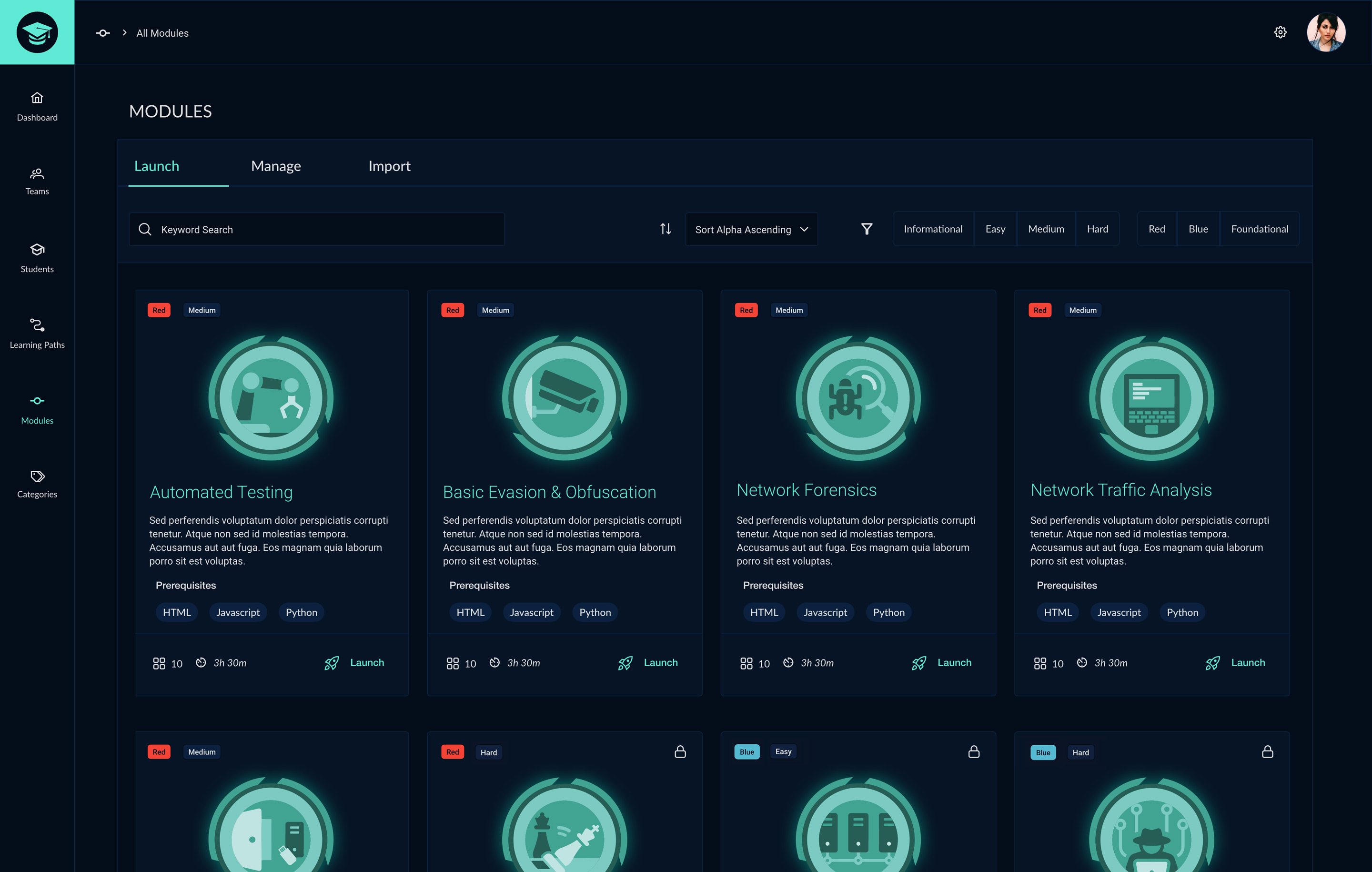
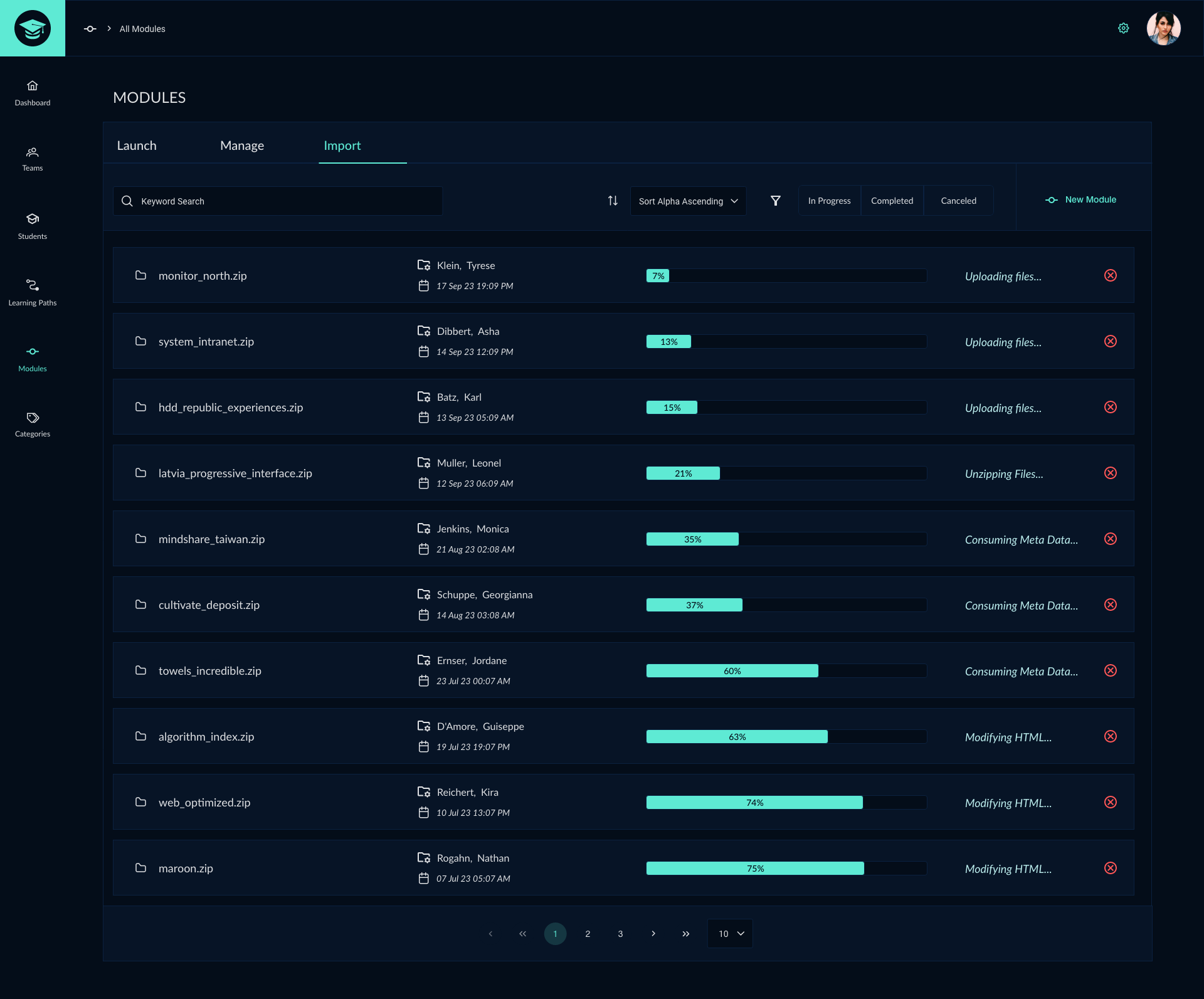
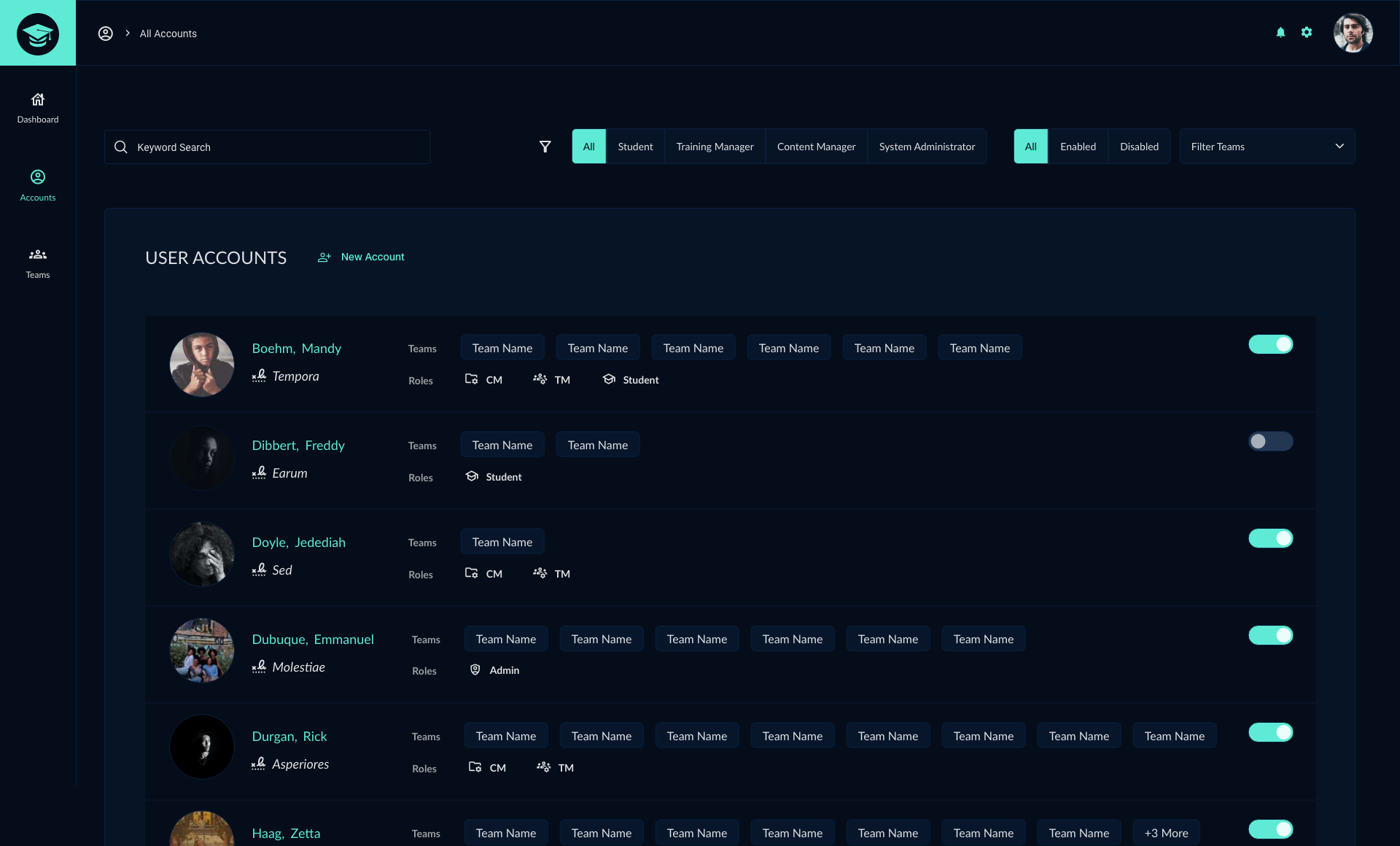
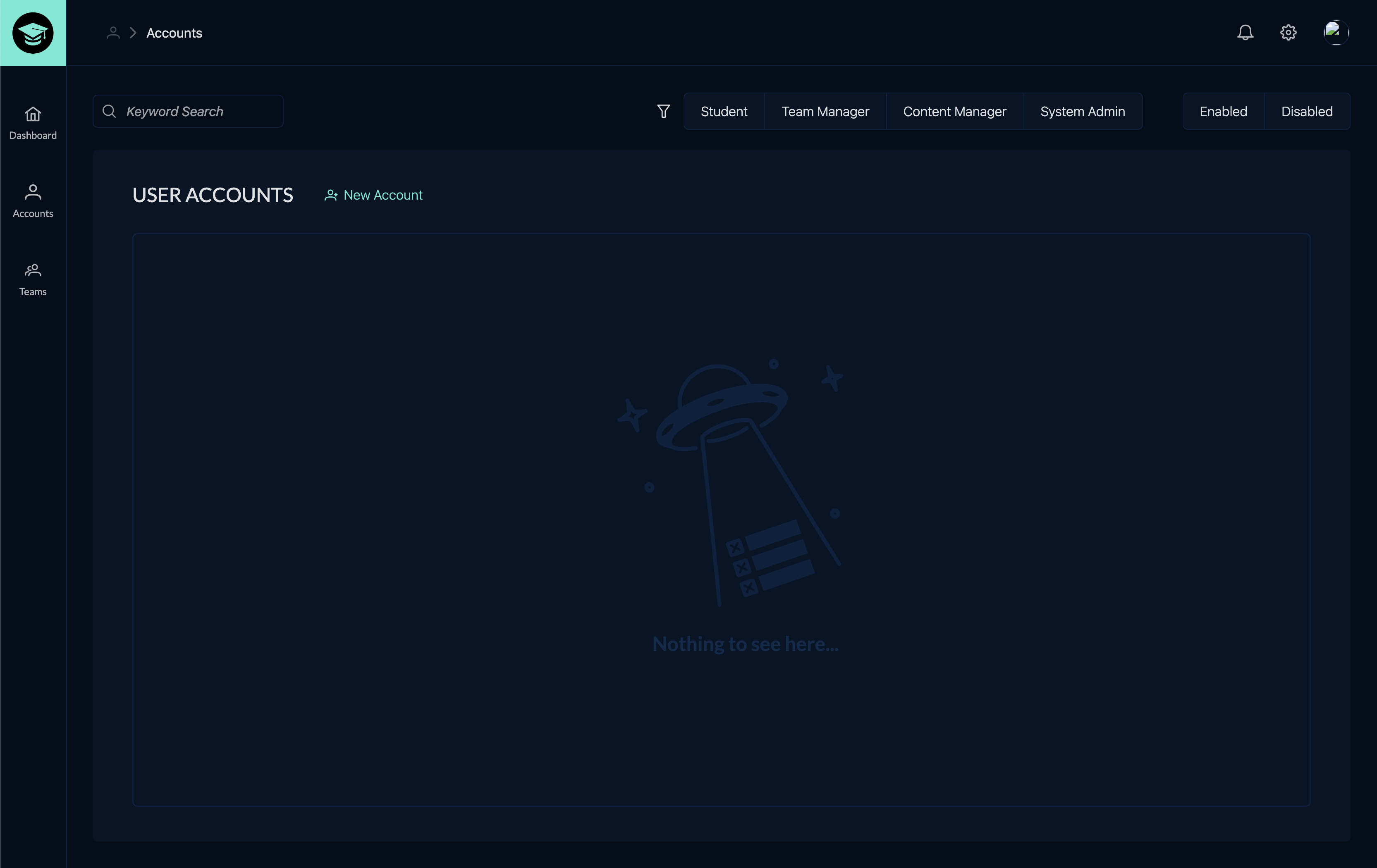
The CyberGrad software application was created to train users on the basics of cybersecurity through interactive lessons and quizzes. Our team considered using a pre-built Learning Management System to complete the project but instead opted to create an original custom application. My responsibilities for the CyberGrad project included:
cybergrad software application
#ui/ux #frontend #css #tailwind
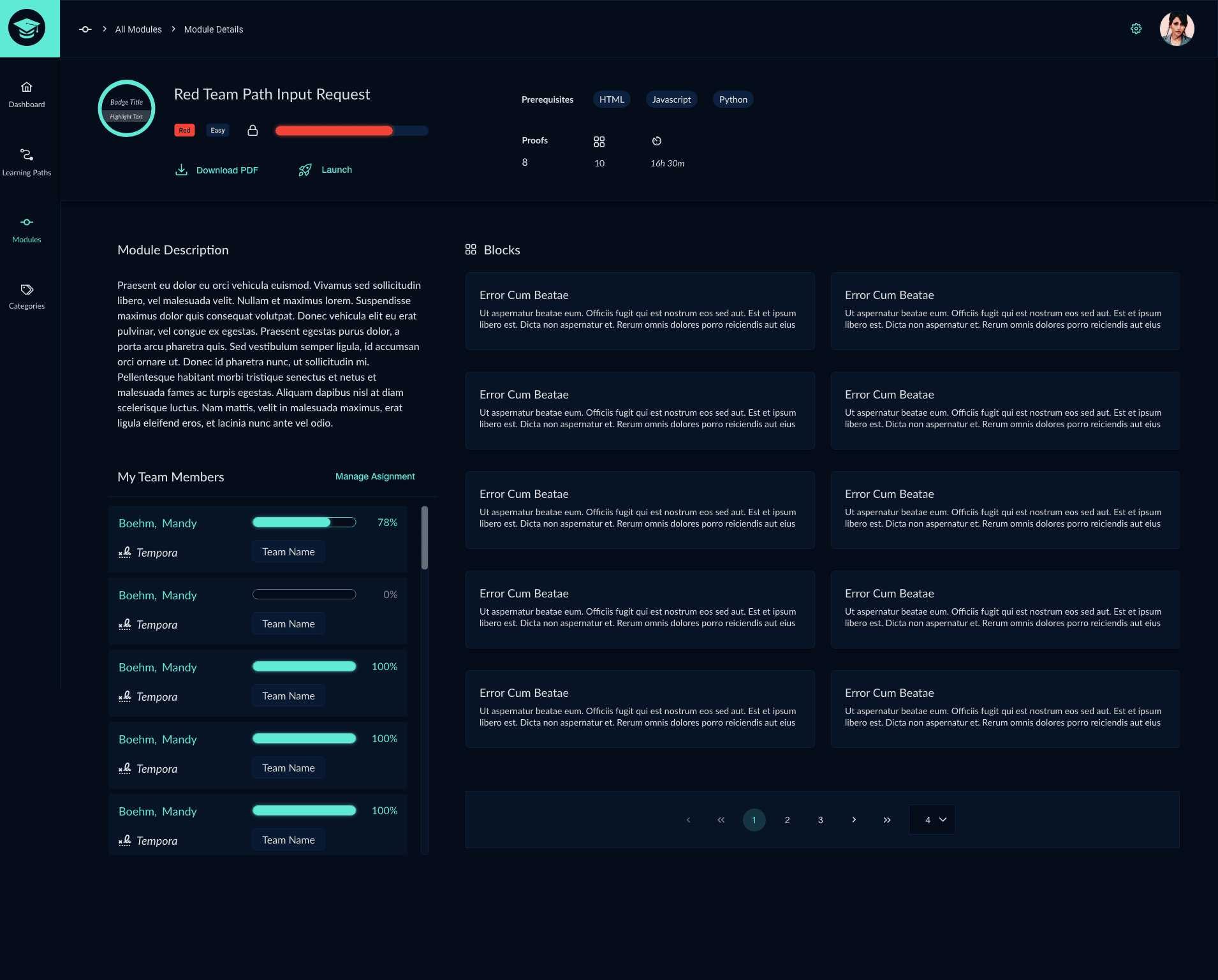
Cybergrad was developed in collaboration with Red Team training experts k>fivefour who created the red and blue team lesson material. My main responsibility in this project was to design UI/UX features for the cybersecurity training application. As a team, we decided to create a new custom application rather than start with an out-of-the-box software solution which resulted in a higher quality design and a better experience for the user. In addition to assisting with the app's UI/UX, I was responsible for creating the logo and lesson badge sets.
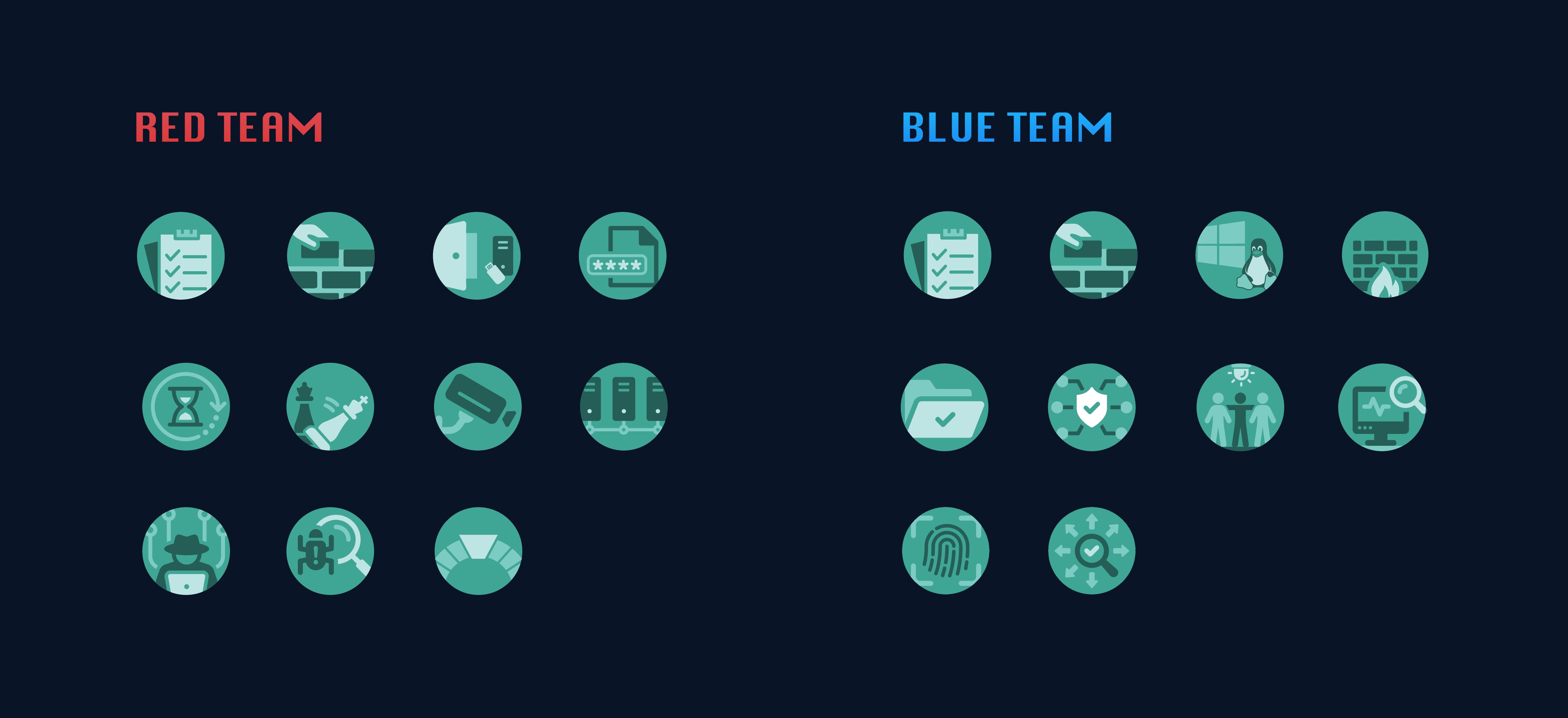
cybergrad lesson badge set
#graphics #design
For the CyberGrad project I was also tasked with creating a custom set of badges to be used by both instructors and students to track completed course work. Below are some example badges from both the blue and red team badge sets.
Adversarial Tradecraft
The study of the tactics, techniques, and procedures used by cyber adversaries to exploit or compromise computer systems, networks and info
Network Forensics
Discovery and retreival of info surrounding a cyber attack including recording events and finding the source of an attack
Initial Access
Learning the different available paths for gaining access to the target network environment
Privilege & Escalation
Learning the different available paths for gaining access to the target network environment
Recon & Analysis
Preliminary scanning phase of a cyber attack to gather info about potential vulnerabilities that can be exploited
System Containment
In the event of a security risk blue teams perform identification, containment, eradication, and recovery steps to limit threats
User/File/Process Containment
Containing threats at multiple levels and preventing it from spreading
Lateral Movement & Persistence
Making sure you can maintain your ability to stay inside the network, and move from one machine to another
cybergrad logo
#logo #design #illustrator
As with the entire project, the logo was to be created as an original design. There were many logo ideas submitted by the team, but eventually the name CyberGuard was chosen. However, at the last minute, it was proposed to change the name from CyberGuard to CyberGrad.